What Are Cybersecurity Services? 🤔

Cybersecurity services are professional solutions and strategies offered by experts and firms to protect digital assets—like data, devices, applications, and networks—from hackers, malware, data breaches, and unauthorised access. Think of them as a digital shield for individuals and organisations.
🔐 Types of Cybersecurity Services
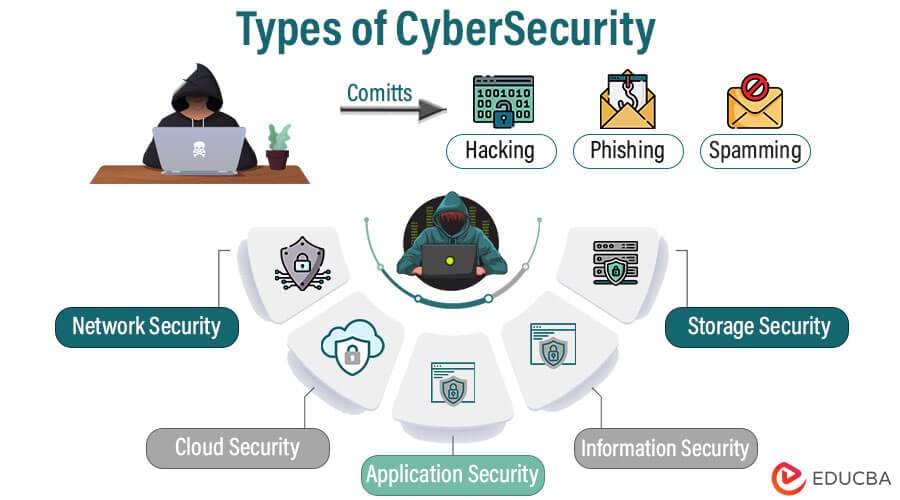
1. Assessment & Auditing Services
- Vulnerability Assessments scan your systems for weak points.
- Penetration Testing (Pen‑Testing) simulates real cyberattacks to uncover hidden risks.
- Security Audits review policies and compliance with standards like GDPR or ISO 27001
2. Incident Response & Forensics
- Incident Response (IR) involves detecting breaches, containing damage, and restoring systems.
- Digital Forensics investigates how incidents occurred, who caused them, and what needs fixing.
3. Managed Security Services (MSS / MDR)
- Managed Detection & Response (MDR) offers 24/7 threat monitoring, detection, investigation, and response by experts using security tools like EDR and SIEM.
- Managed Security Services (MSS) also include tasks like firewall management or threat intelligence without needing an internal team.
4. Endpoint & Network Security
- Endpoint Security protects devices (laptops, mobiles) from malware, ransomware, and phishing attacks.
- Network Security manages firewalls and Intrusion Detection/Prevention Systems (IDS/IPS) to secure network traffic.
5. Cloud & Application Security
- Cloud Security safeguards cloud infrastructure, apps, and data with continuous monitoring and compliance measures.
- Application Security tests software for vulnerabilities and protects against injection attacks, weak authentication, and more.
6. Identity & Access Management (IAM)
- Controls who can access what, using technologies like Multi‑Factor Authentication (MFA), Single Sign-On (SSO), and Identity Governance.
7. Security Information & Event Management (SIEM)
- Aggregates log and event data to detect anomalies in real time. Often used in SOC or outsourced SOC environments.
8. Awareness Training & Consulting
- Educates employees on best practices, phishing, password hygiene, and safe online behaviours.
- Consulting services also include creating security strategies, compliance planning, and policy development.
9. Compliance & Certification Support
- Helps organizations comply with regulations like GDPR, HIPAA, and PCI‑DSS.
- Services may include audit assistance, certification support, like SOC 2 or ISO 27001
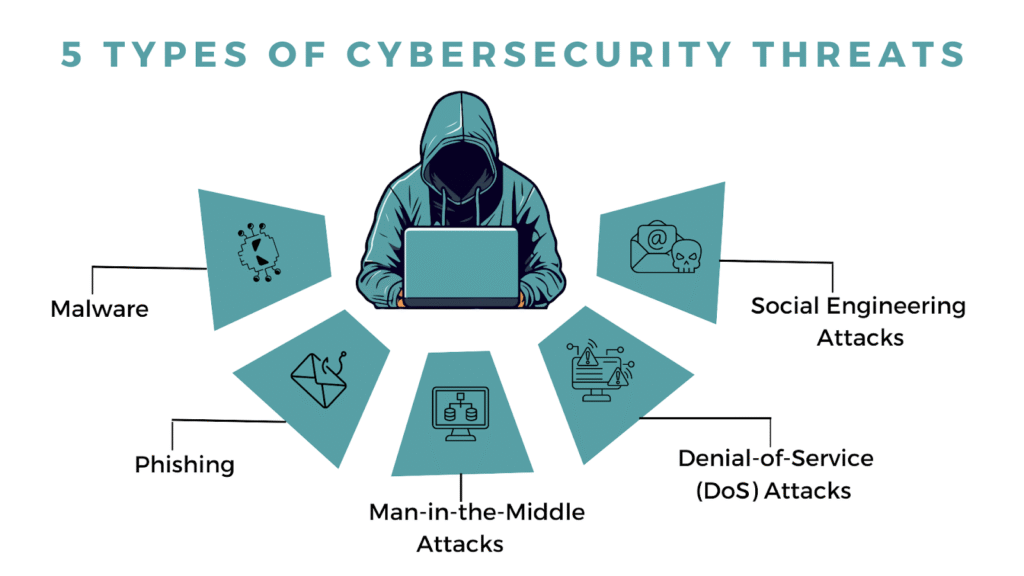
🎯 Why Are These Services Important?
- Prevent serious damage: Cyberattacks can cause downtime, financial loss, reputational harm, and even legal issues.
- Track & catch hackers: Continuous monitoring detects threats quickly—before attackers can embed themselves. Investigators then track breach origins and damage.
- Build trust: Compliance and a strong security posture help businesses maintain customer trust and regulatory standing.
- Manage complexity: With rising AI‑driven and automated threats, organisations often rely on consolidated services like MDR to avoid tool sprawl and operational fatigue.
✅ Effects & Public Impression of Cybersecurity Services
- Organisations that invest in these services often avoid costly breaches, ensure continuity, and build credibility.
- End-users and customers feel safer and more trusting when they know systems are monitored and secured.
- Effective training reduces the risk of human error, which is a leading cause of breaches.
- Firms seen using consulting + tech + training, + compliance tend to have a reputational edge.
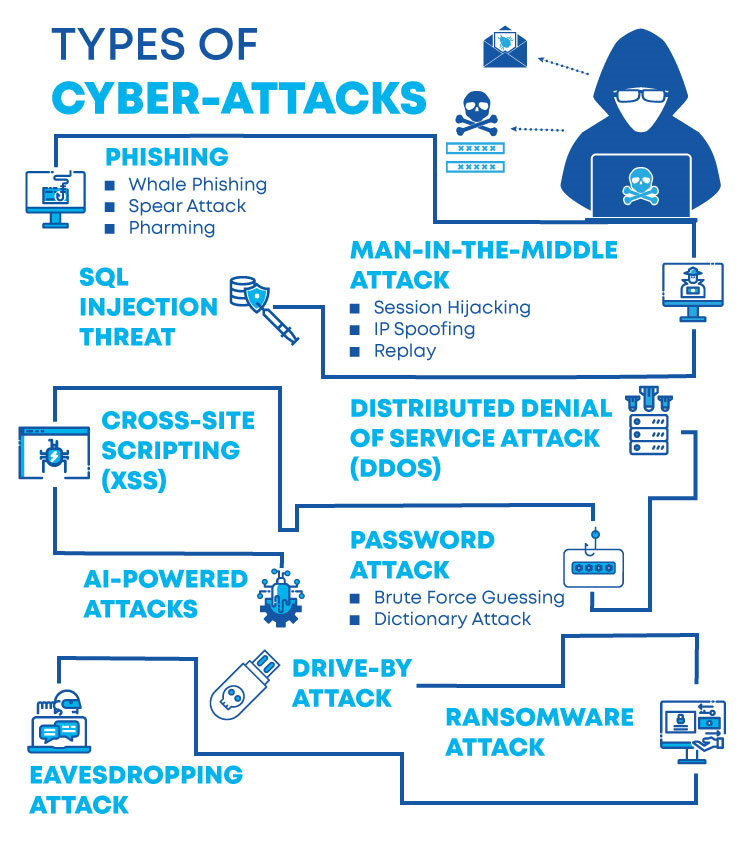
🛡️ How Cybersecurity Services Fight Against Hacking & Tracking
- Hacking: By performing penetration tests and vulnerability assessments, providers identify holes before attackers do. Then they install protections like firewalls, IDM, and endpoint defenses.
- Tracking & Surveillance: Services like threat intelligence monitor hacker activity trends. SIEM tools sift through logs and user behaviours to flag suspicious access that could indicate tracking or misuse.
📌 Summary Table
| Service Category | Purpose |
|---|---|
| Assessment & Auditing | Find vulnerabilities |
| Incident Response & Forensics | Respond to and investigate incidents |
| MDR / MSS | Real-time monitoring and expert threat handling |
| Endpoint & Network Security | Protect devices and network infrastructure |
| Cloud & App Security | Secure cloud-based systems and codebases |
| IAM | Manage secure access rights |
| SIEM | Detect anomalies across all systems |
| Training & Consulting | Build awareness and strategy |
| Compliance Support | Meet legal and industry standards |










